Blockchain and cryto
Purpose of blockchain
with a blockchain we can decentralize where code runs and agree on the output
- there’s no single owner of the code’s execution
- the code always run as a program.
- the code transparently verifieable.
the purpose of blockchain is to have a network of computer agree upon a common state of data.no person or organization can control this, erevryone should be able to practicipate in this process.
- the code transparently verifieable.

blockchain network
- blockchain: protocal connecting these machines.
- each machine or node will in the network will run code as it is writen.
- the blockchain will enforce these rules.
- since the program is enforced, it is called “smart contract”.
bitcoin
- the first successful blockchain and crypto.
- but there was much research and attempts before it
- a lot of components were discovered today.
how it works
- proof of work - Security.
- mining the rewards - fiancial incentives.
- public key cryptography: Authenication.
- linked data structures: chronology.
- peer to peer connection: permissionless.
these components work together in concert.
decentralization emerges from a properly setup network
Cryto
way before crytocurrences, there was cryto.
two important primitives for our purposes:
- crytographic hashes
- publick key crytography.
hash function
hash: give me a input I’ll give u a fixed size output
input can be any type of data: image, string, video.
crytographic hash function
a crytographic hash is a function with these properties:
- deterministic
- pseudorandom
- one-way
- fast to compute
- collsion resistant.
sha256 is one such function which provides 256 bit outputs.
crytographic hash functions
two important use cases for hash functions for us:
- commitments(smart contract)
- proof of work
digital signature
symmetric key
same key on both sides.
communication security over an unsecured channels.
history
- military
- key:324, msg: cat, encrypted: dog.
example:
aes: advanced encrypted standard.
downside: bothside must have the key beforehand.
- key:324, msg: cat, encrypted: dog.
Asymmetric key
one public key, the other private key.
public key signs (encrypted).
private key verifies. (decrypted)
commonly referred to publicKey crytography.
publick key in web3
- users sign a transaction with their private key.
- user boardcasts the transaction to blockchain.
- blockchain nodes recover public key from signature from which the user’s address is derived.
RSA & ECDSA
RSA based on publick key methonology. it’s very easy to find the product of two prime numbers, yet extremely difficult to factor out those two prime numbers if you have the product
The ECDSA algorithm uses elliptic curves. It can provide the same level security as other public key algorithms with smaller key sizes, which is the reason it’s become quite popular. It is the Digital Signing Algorithm used by Bitcoin, specifically the secp256k1 curve.
proof of work and mining
mining key points
- mining is the process to create a block of transaction to be added to blockchain.
- peers in the mining process are called ‘miners’
- a. to network
- b. miners provide processing power to network to exchange for chance to get rewards.
mining has two main functions:
- consensus machanism
- currency issuance
in a decentralized enviorment we always have those issues:
- how do all nodes agree on what current and future state of users account balance and contract interactions is?
- who gets to add new blocks/transactions to a chain.how do we know any blocks added are ‘valued’
- how we know all of these thing condinated without any central actor in place?
the solution of those is consensus mechanism
consensus mechanism
consensus mechanism means comming to a general agreement. blockchain consensus mechanism typically means that at least 51% of nodes are in agreement over the current global state of the network.
the main consensus mechanism rules for proof-of-work typically look like religious commandments:
- cannot double spend
- the longest chain will be the one the rest of the nodes accept as the one “true” chain, determined by a chain’s cumulative work. also known as nakamoto consensus.
mining algorithm
when a miner ‘mines’ a block, what does the miner actually do?
mining software continously hashes a block until a hash is fount that meets a target difficulty.
nonce
sha256("Hi Grandma! coolgrandma555@hotmail.com 0"); // f2d9e2…
sha256("Hi Grandma! coolgrandma555@hotmail.com 1"); // 4ee36e…
sha256("Hi Grandma! coolgrandma555@hotmail.com 2"); // c25e5c…
// keep on guessing, keep on guessing…
sha256("Hi Grandma! coolgrandma555@hotmail.com 424"); // 5552ab…📖 The number that we’re appending on the end of the message here is generally referred to as a nonce. We’ll see how both Ethereum and Bitcoin make use of nonces in a few ways!
blockchain structure
The image show three different ways of internet. the first way is centralized for trandional applications, if u want prove value, it decide by centre services. the second way is Decentralized, it always be missunderstanding to blockchain. but blockchain have a important way, it is peer to peer. so the last image shows blockchain.
thought challenges
Q: how do distributed p2p networks agree on what data is validated without a central administrator running the show?
A: Consensus machanisms
- the bitcoins network decides validity of new data based on who is able to produce a prove of work.
Q: how is the block hash calculate?
A: the hash function takes data as input and returns unique hashes.
Q: what is ‘valid’ hash?
A: A valid hash is meet certain requirements.
- block index is greater than last block index.
- block previous hash is equal to lastest block hash.
- block hash meets difficulty requirements.
- block hash is correct calculated.
UTXO & Account Models
trandional vs p2p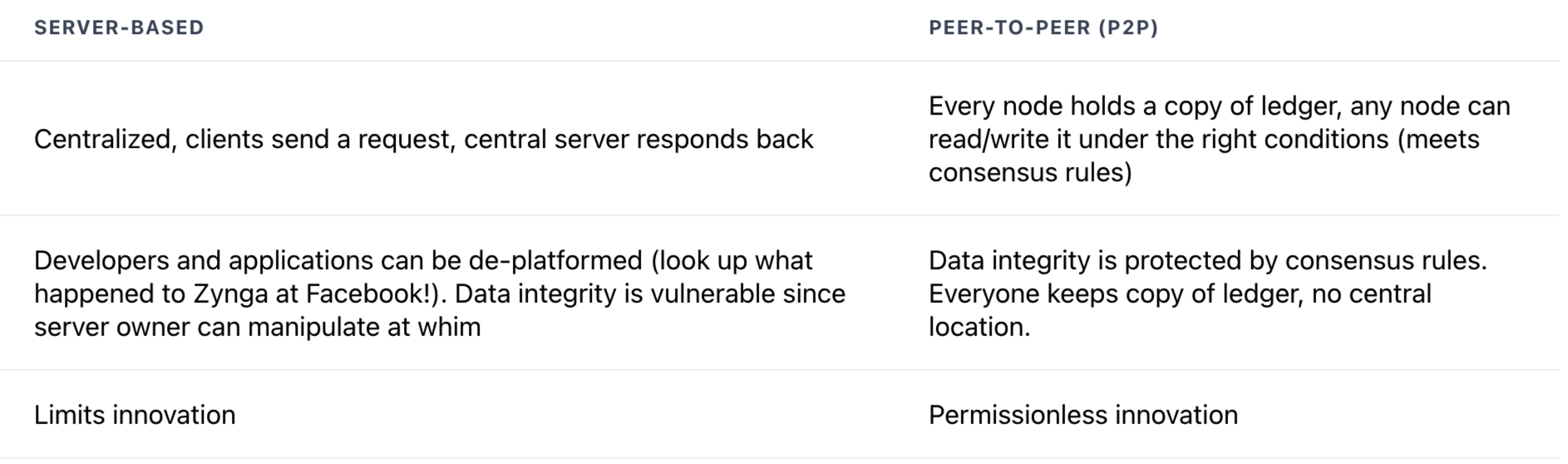
Nodes in blockchain p2p network, like bitcoin, can leave and re-enter the network at will. bitcoin has nodes inclding the light nodes and full nodes.
light nodes: a light node downloads only the block headers , which is the minimum data it need to transact on the network. a light node can validata a transaction because it is able to regenerate the spcific block it need to check by using this data. but this also have limitations, Light nodes will sometimes need to ask full nodes for the data they don’t have access to, whilch could take longer than a full nodes validating the transaction.
full nodes: a full use and storage of data means that full nodes require a lot of computing and bandwidth resources. a full nodes download, stores, and verifies the full blockchain state-everything from block zero to the most recent blocks, which can take a weeks to sync.
achieve nodes: a full node trims entires that is no longer needed to verify, the latest interaction with the chain, the achive nodes maintain everything. these details are greating for querying information more efficiently and handy for a few applications, but are excessive for most case.
Account models
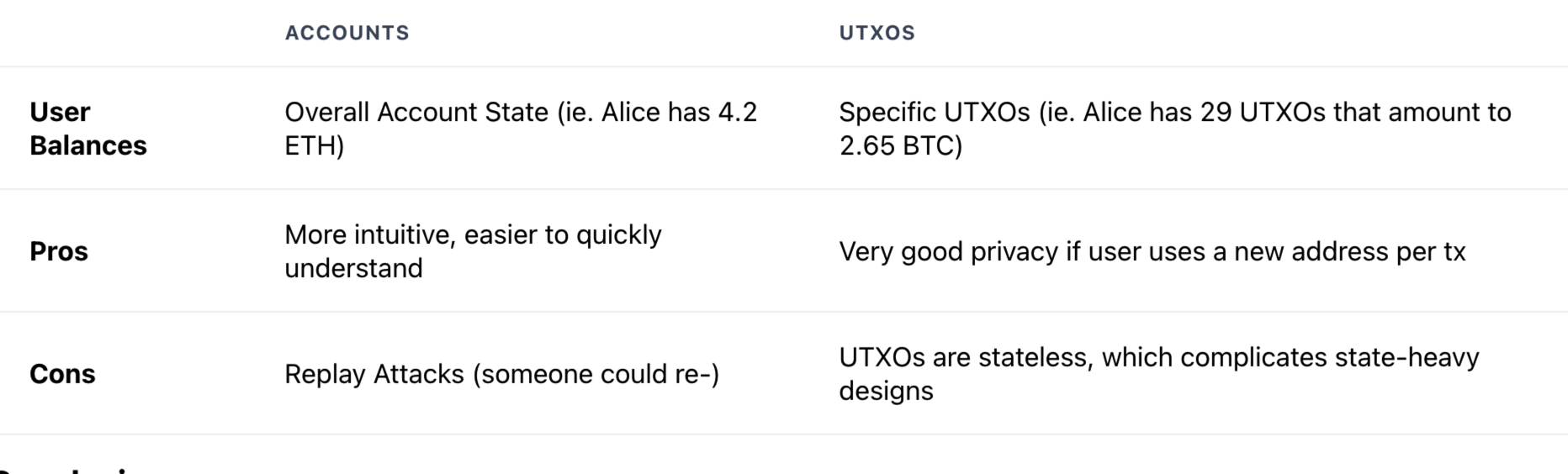
If you have a bank account, you are very familiar with this model of keeping track of user balances. The account model follows just that: accounts. It tracks the balances of users based on their overall account state, without any tracking on what constitutes the actual balance itself. In other words, an account-based ledger would mark an entry like this:Acct #12345 -> Name: Rick Sanchez -> Balance: $142.62
Notice how the state of the account is kept very high-level? Rick’s account balance is a dollar and cent amount and that’s it. There is no further information tracked on what the breakdown of the the balance is, for example: $142.62 is one $100 bill, one $20 bill, two $10 bills, eight quarters, five dimes, two nickels, two pennies. When Rick goes to an ATM and withdraws from his balance, he gets it in whatever bills + change the bank has at hand - not in the exact change it took to make up that balance in the first place.
What does a transaction look like in an account-based model?
Alice has $60 total balance
Bob has $20 total balance
Bob sends Alice $5
Bob’s balance is subtracted $5, if the remaining balance is greater then 0, proceed, else revert
Alice balance is summed $5
The ledger is marked in both ends to update total balances and that is the end of the transaction in an account-based model.
This might seem weird. Why would we want to keep track of these details for something as simple as a total balance? We’ll look at a model for keeping user balances that does include this feature: the UTXO model.
UTXO
Ethereum uses the account-based model, while Bitcoin uses UTXOs (short for Unspent Transaction Outputs) to keep track of user state/balances.
The UTXO model differs pretty drastically from the account model. It’s a little bit more complex - mainly because it is not a familiar interface like the account model is! Yet it does set up some interesting features…
What is a UTXO? 🤔**
Alice sends Bob 5 BTC in the form of a transaction relayed to the Bitcoin network. At this point, if the transaction is valid (Alice has > 5 BTC, Alice owns the relevant private keys and can produce a signature, etc), Alice is signaling an intent to change user state. When the Bitcoin network mines Alice’s transaction, Bob is credited with a UTXO worth 5 BTC. This is how the Bitcoin network keeps track of user balances - it keeps a really big long set of UTXOs - outputs out of state-changing transactions that credit users with a certain amount of BTC.
So when people say: “I own 3 bitcoins”, they should really be saying: “I own some UTXOs that allow me to spend 3 bitcoins.” - or using the Drake meme:
Account vs UTXO
conclusions
Deciding what model to go with is a game of design tradeoffs. Ethereum uses the account-based model transactions must be more flexible to account for the many moving pieces of state in the system. Bitcoin uses UTXOs as it is a network purposefully designed to be as simple and stateless as possible.
scriptPubKey
scriptPubKey also called “witness script” or the “locking script”.
for each locking script there should be an unlocking script that will unlock the UTXO and allow it to spent. typically, all the unlocking scripts needs to provide is a signature for to verify ownership of the public key. then the public key need to match the address after two hashed twice.
Here have a interesting things, the first block of bitcoin( or called genesis block ) can’t be spent because it don’t have coinbase, we don’t why Satoshi don’t give the block coinbase. but if a block that don’t have coinbase, thus all of the nodes will reject the transaction. so we never spent! it’s fovever bount to 1A1zP1eP5QGefi2DMPTfTL5SLmv7DivfNa.
bitcon script
the bitcon script language is meant to be a simple stack-based that has no loops so it also will be resolved and there are no denial of the service attacks. the language is basically a list of function like operations code.
<a href='https://bitcoin.stackexchange.com/questions/29754/history-behind-the-scripting-language-in-bitcoin/29763#29763'> bitcon script history</a>
aka
ethereum: 以太坊
Blockchain: 区块链
Crypto: 加密
crytocurrencts: 加密货币
decentralized: 去中心化
bitcoin: 比特币,第一个基于区块链技术实现的加密货币
fiancial incentives: 金融奖励
mining the rewards: 挖矿
deterministic: 确定性
pseudorandom: 伪随机
collsion resistant: 抗碰撞
consensus: 共识,一个网络对数据的状态达成共识。
censorship:审查
bribe: 贿赂
drill home: 钻研
relatively travel:相对较小的
infeasible: 不可能
symmetric: 对称
digital signature: 数字签名
RSA: 非对称加密的经典实现
ECDSA: bitcoin采用的非对称加密算法
ether: 以太币
address: 交易发起方类似于ip, bitcoin 使用checksum and base58, ethereum is last 20 bytes of the hash of the public key.
Enforcement: 执行
consensus rules: 共识规则
consensus mechanisms:协商一致
inter-changeable: 可互换的
cumulative: 积累型
nakamoto consensus: 最长的chain将是其他节点接受的一个真正的链,他是由一条链积累的工作所决定的。
txs: transactions.
pos: proof of stack, pos中,参与者需要持有一定数量的crytocurrency,参与记账过程,相比pow,pos不需要大量的算力
pow: proof of work,miners通过计算来添加txs和block,需要消耗算力。可以增加security of blockchain
merkle root:默克尔根,用来验证和确认交易是否被篡改。
underlying: 底层
hashcash: Hashcash工作量证明功能由Adam Back于 1997 年发明,并建议用于反 DoS 用途
Byzantine General’s Problem: 在p2p场景下,如何证明每个机器都是在工作的。
manipulate: 操作
Genesis Block: 第一个加入到区块链中的块,初始块
cost-effective: 成本效益
UTXO:Unspent Transaction Output, 未使用的交易
Retrospective: 回顾
vulnerable: 脆弱的
light nodes: 轻节点 (存储块头的轻节点)
full nodes:完整节点(常规节点)
achieve nodes: 归档节点, 完整节点(已验证的存档节点)
bandwidth: 带宽
configure: 配置
variables: 变量
discrepancies: 差异
tradeoffs: 权衡利弊
contrast: 对比
unfakeable: 不可伪造
replicate: 复制
Satoshi: “Satoshi” refers to the smallest unit of the cryptocurrency Bitcoin
individual: 个人
multitude: 众多的
aggregate: 总数
expedite: 加快
hefty prize : 巨额奖金
controlled supply: 受控供应
intentional: 故意的
quirk: 怪癖
denial: 否认
distinguish: 辨别
preceding: 前面
emerge: 出现
hierarchically: 层次分明
intimidating: 令人生畏的
underneath: 底下
infacting:连接
concatenate: 串联
optimization: 优化
inconsistencies: 不一致
deveration: 推导
arbitrary: 随意的
immutable: 不可变
implications: 含义
ledger: 账本
traversing: 遍历
PMTs: Partricia Merkle tries
sealed: 密封.



